VIAVI Solutions
VIAVI Solutions 


VPN Performance Validation
How secure are secure tunnels?
The challenge many of us face today is understanding how secure our data is, especially when it is stored offshore on a cloud managed platform. The communication of data securely between two sites is one of the major issues facing IT systems today. The challenge is further compounded when the applications in use are latency sensitive.
Recent online events have shown that the time needed to gain access to sensitive data is minutes! Reports show that a dictionary type password attack or brute force attack can forcefully provide access to a protected network and data storage devices in less than quarter of an hour. Sadly, the explosion in cheap computing power and personal on social networking communities is making the criminal’s job far easier.
Download the white paper to find out how the challenge in maintaining application quality in secure VPN tunnels is greatly simplified by using TeraVM.
By submitting this form, you are also granting VIAVI Solutions permission to send you emails about related topics in accordance with our Privacy Policy. You can opt-out at any time by clicking the unsubscribe link in our emails.
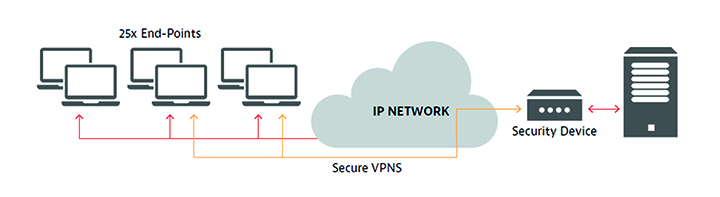
The inclusion of a VPN tunneling appliance